Top 5 Data Security Priorities for Associations

Written By Rick Bawcum
November 10, 2020 | Cyber Security, Data Architecture & Governance,
We’ve got something to get off our chests: following baseline data security regulations doesn’t automatically equal top-notch security.
But let us explain.
If you’ve been keeping up with the trends (which we’re sure you have), you already know that data is now the currency of the modern digital economy. And you also know that in such a digitally connected world as the one we live in, organizations are constantly exposed to new liabilities.
What you probably don’t know is that the government-mandated requirements you are meeting does almost nothing for you, unless you also tailor these requirements to the needs of your organization’s risk management profile. But this is a painstaking task requires both a survey of the current regulatory environment and a practical cost/benefit analysis.
Even if you are up-to-date on compliance standards, the only thing you’ve really avoided are government fines for another year. And if you think being compliant means your data is safe, (we hate to say it) but you have another thing coming.
Below is a curated list of some of the challenges your association will face in 2020.
Top 5 Security Priorities
- Data security
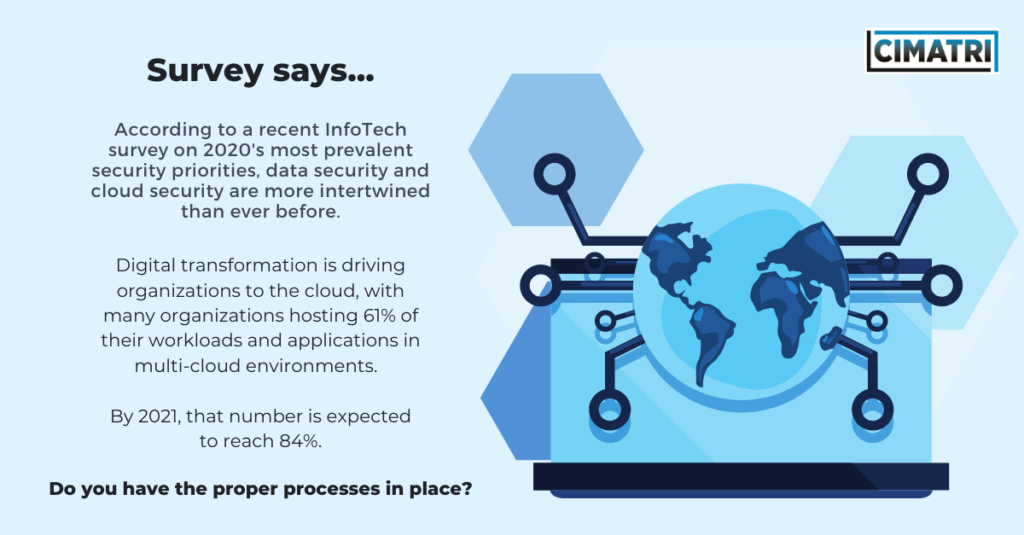
According to InfoTech’s Security Priorities Report, 43% of respondents stated that data security was a top priority for 2020, tying with cloud security.
As organizations move to the cloud, the confidentiality, integrity, and availability of data is vital. With new compliance regulations on the horizon, governments have stepped in to enforce the privacy of data subjects, but it is still up to security professionals to ensure policies are implemented and enforced.
Data security isn’t something that can be approached on an ad hoc basis. Organizations must leverage expertise from privacy officers, security risk managers, and enterprise risk managers to build a framework that ensures their data security program encompasses both security and privacy.
- Cloud security
In 2020, an average of 79% of organizations’ applications and workloads are hosted in some variation of the cloud, and that’s only the beginning. Cloud adoption rates continue to rise as most organizations desire the flexibility and availability that comes from private, public, hybrid, and multi-cloud environments.
But let’s talk about the elephant in the room: shared security.
You must do your due diligence and read the fine print when it comes to who will be responsible for securing what’s in the cloud.
Increased visibility, security as code, and better resilience are just some of the advantages cloud providers offer as security controls to protect organizational data. But internal security measures must still be implemented to protect the organization’s cloud environment.
How?
- Establish service-level agreements that align security obligations with business goals
- Determine compliance regulations
- Define policies and procedures tied to identity and access
- Properly configure your cloud environment using vendor-provided tools
- Secure your applications with a web application firewall
- Email security
With over 165,000 reported domestic and international incidents (costing over $26 billion in lost revenue) from June 2016 to July 2019, email security is generally considered the number one point of contact for hackers. And 2019 was no stranger to convincing social engineering techniques, with coordinated phishing, spear phishing, CEO to CFO spamming, and email spoofing.
So it comes as no surprise that email security authentication protocols must be put in place alongside traditional email security tools to protect against data loss and authenticate senders.
But email security gateways can only provide so much defense, as human error is still the hardest obstacle to overcome.
The easiest way to get started ensuring email security? Provide regularly-updated, mandatory employee training.
- Security risk management
As companies start to transform to meet the opportunities of the digital economy, they also increase the opportunity for failure. Security professionals have to keep up with not only threat actors’ new tactics, techniques, and procedures but also with the speed of business. Organizations must adapt to the agility of business by integrating their governance, risk, and compliance obligations.
Without proper security risk management, the speed at which business now moves provides the opportunity to succeed or fail much more quickly. An up-to-date risk program can ensure the right metrics are communicated to the board so they can align their strategy with risk (read: everyone should make risk-calculated decisions, not just Security).
You need a proper risk governance structure in place or a repeatable and manageable process to assess risk on a per-project basis. Align your business objectives with the privacy and compliance requirements necessary to do business and the security controls that will protect, refine, and review your organization’s risk as it changes.
- Security awareness and training
If organizations hold regular security awareness training, it is usually impersonal and easily forgotten. Humanize your security awareness and training programs to embed security as part of employees’ daily jobs.
Security awareness and training must persist after onboarding. Employees must know the importance of security in business, understand how to protect their and the organization’s data, and enable coworkers to improve their security knowledge and practices.
The first step? Establishing an in-person, collaborative program for security awareness and training that is managed and measurable.
The Wrap Up
Security culture comes from a strong security awareness and training program that socializes security as part of everyday operations. As such, security must inform the overall business strategy. Security risk management encapsulates IT security as an enabler of the business, not as an obstacle.
For more information on cybersecurity and to see what others in the association industry are doing, check out our latest survey here: THE STATE OF CYBERSECURITY




