Establishing a Data Protection Plan: The Complete Guide

Here are the facts:
- The average total cost of data breaches in 2021 skyrocketed from $3.86 million to $4.24 million.
- 56% of IT decision-makers say targeted phishing attacks are their top security threat.
- Hackers attack every 39 seconds, on average 2,244 times a day.
- The average lifecycle of a breach is 314 days (from breach to containment).
It’s time to give your data the protection it deserves by building an effective strategy that goes beyond backups and managing the red tape. This guide explores the best practices and step-by-step process to develop a data protection plan that supports your business continuity goals and growth prospects.
Why is It Important?
Keeping up with the data economy and digital transformation.
The data economy has ushered in a paradigm shift.
Today, data is at the center of system architecture, and transparent privacy cultures are now wrapped into the overall culture and "story-brand" of many organization. Digital transformation journeys are also gaining momentum and deepening in maturity. Data is at the heart of these disruptions.
A strong data protection plan helps you reorient your people, processes, and technology to the sink-or-win reality of today and the race towards continuous process improvement.
Cutting through the red tape stifling progress.
A strong data protection plan helps you avoid legal action from external watchdogs in the U.S. and around the world. Without a plan in place, this red tape often results in slower decision making, new bottlenecks in the flow of information, and multilevel accountability flaws between the top and bottom of the organization.
These data silos and information blockades undermine the productivity, engagement, and morale of staff, creating ripple effects on your ROI, IT investments, and change initiatives.
The first step to combating these risks is to create a strong data protection plan.
The Challenges
Business continuity requirements are often vague.
Not knowing precise business continuity needs often results in over-expenditure and overexposure to liability.
The ever-growing threat spectrum of increasingly organized attacks.
Rising ransomware-as-a-service attacks and cyber vulnerabilities means organizations must mind the gap between security principles and practice. With the heightened risk profile of IT environments and operations, you can no longer afford to ignore the disconnect between strategy and real, practical action.
The regulatory environment is rapidly evolving.
Your data protection plan needs to support the evolving definitions of “personal information” and “personal data,” and changing regulatory goalposts . However, multiple data protection plans are costly and insensible.
Backup options are abundant.
Disk, tape, cloud? Each has drawbacks, efficiencies, and cost factors to be considered.
Backup infrastructure is never greenfield.
Any organization with a history has software to run backups, and that existing software was probably determined by past architectures that may not reflect the diversity of your current cloud, PaaS, IaaS, or on-premise assets.
Our Advice
Don’t let failure be your metric.
The past is not an indication of future performance. Quantify the cost of your data being unavailable to demonstrate value to the business.
Determine the current state of your data protection strategy by identifying the pains and gains of the solution and then create a business-facing diagram to present to relevant stakeholders.
Stop offloading backup as the last resort.
Human error more frequently leads to data loss than any other factor. As such, data protection can’t exist in isolation. Get key leadership involved to ensure you can meet organizational requirements.
Some data is useless.
Stop data hoarding and start protecting what matters. Take the time to understand the data that exists within the organization.
This step is critical to effective data governance and cost management for your data protection program. Neglecting to properly tag and classify data will lead to a costly data protection solution that protects redundant, useless, or outdated data.
How to Establish a Data Protection Plan

Phase one: Define the current state of your data protection plan.
Not all data protection methods are created equal.
Using your backup as your archive isn’t cost-effective. Keeping multiple copies of “cold” data intensifies capacity demands and introduces multiple (possibly disagreeing) copies of important data. A strong archiving policy requires better indexing and search capabilities than needed by backups.
Remember that your data protection strategy isn’t about backing up data. It’s about being able to access and restore your data in an appropriate amount of time.
Identify the drivers behind your data protection strategy
Understanding the drivers motivating your organization’s backup strategy ensures that the implemented solution provides returns exactly where you need it most.
To get started, book a meeting with key stakeholders to outline the purpose of your future backup software and the drivers behind the decision. Then, document your plans with your drivers in mind.
Align key drivers of your strategy with your association’s goals
Ask yourself:
- What are the IT initiatives around data protection and business continuity?
- What data protection services do we currently have in place?
- What are our critical business activities?
- What applications and data sources are associated with these activities?
- How are we currently backing up that data?
Analyze problems found in your current backup solution
Meet as a group to brainstorm issues and shortcomings with your current backup solution. Then, try to match those problems with solutions where applicable. These potential solutions will be useful when searching for new strategies or when fixing your current solutions.
Phase 2: Conduct a Business Impact Analysis to understand data restoration requirements.
You must know what you’re backing up and why. “Everything and forever” is not a viable answer.
When it comes to recovery, you must maintain a delicate balance between budgetary constraints, recovery objectives, and data security. And while the budget is typically fixed, you must still ensure that your data recovery objectives are, first and foremost, based on your organization’s needs.
But in order to meet those needs, there needs to be a clear line of communication between your core team members and users to understand what you can give and where. To develop practical backup procedures, you need to determine the recovery objectives your data and applications need.
And remember: data backups are about minimizing loss - not eliminating it completely.
Sure, in an ideal world, you would be able to recover from an up-to-the minute backup with the snap of your fingers, but in the real world of dollars and cents, this just isn’t feasible (or needed).
Why bother with a business impact analysis?
In the association industry, you’re constantly stretched thin, and we get that, but that doesn’t mean your data restoration strategy should fall to the wayside. In fact, it’s the opposite.
Time is money, and data drives decisions. Conducting a business impact analysis before choosing a data protection strategy is key to saving both. They give you the opportunity to:
- Determine workload criticality.
- Establish appropriate RTOs and RPOs.
- Inform vendor selection and evaluation.
- Justify cost for disaster and operational recovery.
How does the BIA methodology work?
1. Creates objective scoring criteria.
Avoid defaulting to “whoever screams the loudest” getting priority. An objective scoring scale increases the transparency between IT and the business while establishing a consensus on criticality.
2. Keeps the process efficient.
Value versus effort. You want your business impact analysis to be efficient enough to be iterated on and digestible by all stakeholders and team members.
3. Scales to assess the entire environment.
Do. Rinse. Repeat. The methodology you learn is repeatable for the rest of your softwares and applications. By understanding how to run the exercise, you can continue to facilitate informative sessions when systems are introduced. Meaning: when processes change, you’re already one step ahead.
Best practices
Conduct a proper cost/benefit analysis of all the Total Cost of Ownership
If restore and disaster recovery objectives and total cost of ownership are unbalanced, you’re either spending too little or too much.
Conduct a proper cost / benefit analysis of all the Total Cost of Ownership (TCO) aspects to fit at an acceptable cost. But keep in mind that under-protection of data is risky and overprotection of data is costly. More isn’t always better.
Here at Cimatri, we tend to go with the Goldilocks' method. Utilizing best-fit protection of data to safeguard valuable data at the lowest possible cost without compromising quality. (Read: it’s just right, and it’s built specifically for us.)
Consider the cost of data loss
When developing your data protection plan, consider the cost of data loss as well as the cost of downtime in any estimation of restore requirements.
If you were to monetize your data, what would it be worth? If you were to lose your data, what would be the direct costs?
IBM’s annual Cost of a Data Breach Report found that the average total cost of data breaches rose from $3.86 million in 2020 to $4.24 million in 2021, the highest in the report's 17-year history. Compromised credentials was the most common type of attack, responsible for 20% of breaches at an average cost of $4.37 million.
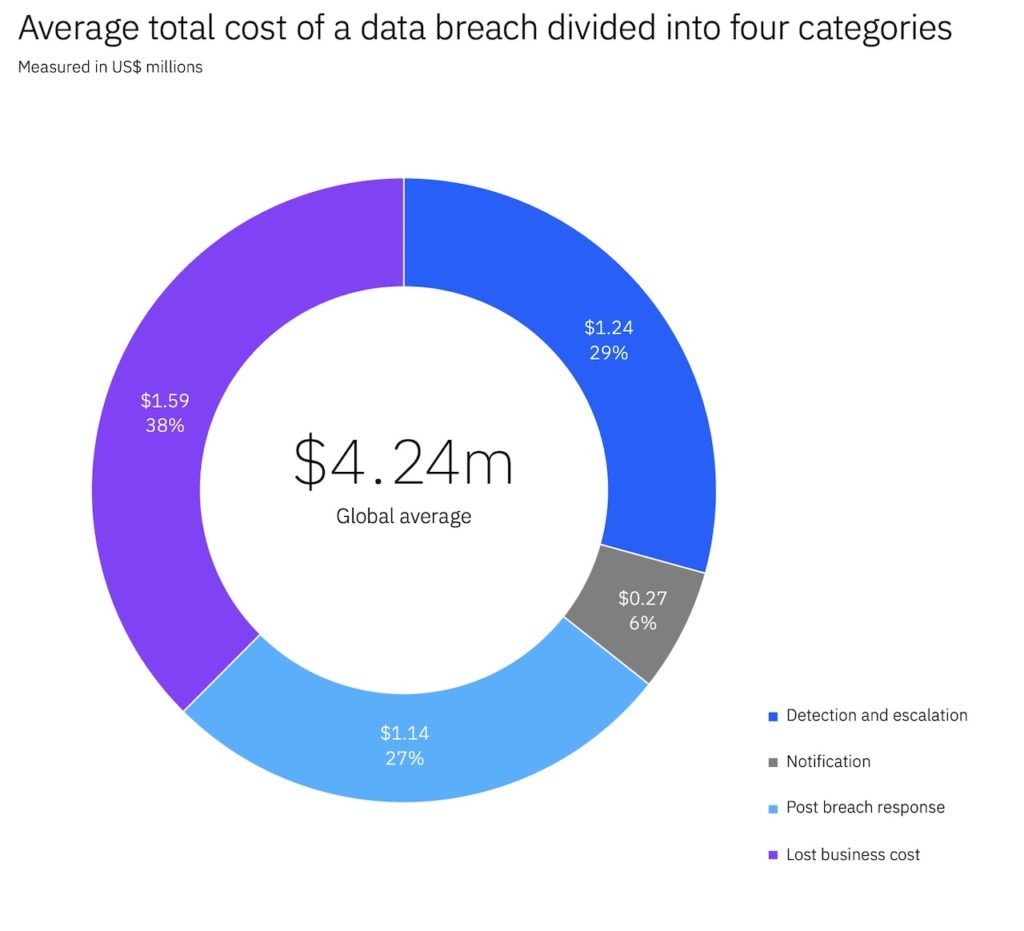
These direct costs should serve as a baseline for what is spent on backup. In other words, match the value of data with the cost to back up and restore to maximize your return on your backup investment.
Adjust to meet your backup window, if necessary.
There are only two ways to better meet your backup window: move less data or move that data faster.
Meeting your backup window is critical to your success. If you don’t complete backups within their allotted time, you risk failing or slowing down day-to-day operations.
And while it is unlikely that your backup window is going to get any bigger, you still have options. You can either reduce the amount of data backed up or increase that speed.
Phase 3: Propose the future state of your data protection plan.
Your backup needs are going to change. And often. Be prepared and agile.
Use information lifecycle management to help define states of care
Backup strategy is not the place for (nor does it require) a full Information Lifecycle Management (ILM)/Data Lifecycle Management (DLM) implementation.
When infrastructure leads the charge on data governance initiatives, they traditionally fail. Ensure that your backup processes respect any ILM that may be in place or build out just enough of one to ensure your own success.
Effective information classifications are distinct from one another in their deployment and application of different standards of care. And while the specifics will vary across your organization, an information lifecycle may help structure your approach so specifics can be easily derived.
Determine necessary attributes for your strategy
Gather a small team to brainstorm. Start by writing the question “What attributes are necessary for our data protection solution?”.
Have your participants write down ideas and points. Then, spend time organizing those notes into logical groupings.
Once grouping is complete, work with the team to define each category. These will be used to determine the necessary requirements for each tier of your data architecture.
For each attribute, drive consensus on what should be required based on the tier of data. These tiers should come from your business impact analysis.

Consider your approach to end-point data backups
End-point data remains a stumbling block for many backup strategies.
End-point devices (i.e. laptops, tablets, and smartphones) are major sources of production data and, as such, are subject to compliance regulations, just like anything else. What’s different, however, is that this data is particularly vulnerable, especially when mobile.
According to IBM's report, for example, the average cost of data breaches in 2021 was $1.07 million higher in remote work situations.
The truth is this: users are frequently the weak link in the chain, and leaving backup responsibilities to your users might mean that the data won’t be backed up at all. And putting in place certain policies that require the end-user to store data in specific locations won’t truly fix the problem.
Where possible, include end-point data as part of an automated backup policy. This will require the support of your users, so it is vital that you communicate with them the risks of not complying with operating procedures. Your ability to correct backup, store, and find their data depends on their cooperation.
Best practices
Make your strategy flexible and plan for change.
As we’ve mentioned before, your backup needs are going to change. And constantly. You need to be prepared to reevaluate your data protection plan as different needs arise.
Clarify your needs.
How much notice will you need to incorporate a new application or software into your backup processes? Make sure your strategy takes this into account. Remember, without sufficient planning, your data may temporarily be at risk.
Document the process for introducing new systems into the data protection environment.
Assume that new applications will receive an intermediate level of service unless there is a business case made for an exception. Consider developing a standard request form and insist that application owners provide you with a detailed rundown of the application’s backup requirements.
Consider future-proofing your data security measures to mitigate cyber risk in a changing world.
Consider these stats based on IBM's Cost of a Data Breach Report 2021.
- Organizations further along in their cloud modernization strategy contain breaches an average of 77 days faster than those in the beginning stages of their modernization journey or those without a digital transformation strategy.
- When fully deployed, security artificial intelligence (AI) automation is the biggest cost mitigator, saving organizations up to $3.81 million compared to organizations without it.
But again, balancing under-protection and overprotection is essential to keep your costs in check while still optimizing your data security.
You also have to account for the dynamic and uncertain regulatory landscape, changing public attitudes towards data privacy and security, and the transition from marketing practices built on first-party and third-party data to the modern era of Zero-Party Data and Privacy-First Personalization.
When envisioning the future state of your data protection plan, you must consider your privacy culture as a whole. Not only is GDPR enforcement rising sharply, but new regulations such as China's Personal Information Protection Law (PIPL) and the Virginia Consumer Data Protection Act (CDPA) are popping up regularly. And the public is more aware of data processes and privacy rights than ever before.
Positioning your organization competitively in the long-term is contingent on your ability to embrace a future-forward privacy culture. In such a privacy-first framework, your data protection plan would be engrained in the design of your software systems and IT processes from the get-go.
The Wrap Up

If there is one takeaway, let it be this: data growth is inevitable, and data protection is vital.
An effective data protection plan starts with working with your team to understand data growth patterns for your organization and anticipating how your capacity needs will change as you grow. Plan for more growth than expected, and plan your budget accordingly.
For many, a great place to start would be an analysis of your current framework and IT applications. Check out our Security Assessment here as well as our new Data Quality Assessment for Associations here.



