What is Cybersecurity: An Overview

Is Your Data Safe?
Once thought of as only required for military outfits and large financial institutions, the cybersecurity field is currently undergoing a massive shift to the mainstream. As the volume and sophistication of cyber attacks grow, all organizations must take steps to protect sensitive information.
Over the course of doing business, organizations transmit information across networks. A significant portion of that data is sensitive in nature (i.e. intellectual property, financial data, personal information, etc.) Cybersecurity, also known as information security (InfoSec), is dedicated to protecting that information and the systems used to process or store it.
What is Cybersecurity?
Cybersecurity can be broken down into four main categories:
1. Risk management
Risk management is the process of identifying, assessing, and controlling threats to an organization’s information assets. These threats may stem from a variety of sources, including financial uncertainty, legal liabilities, strategic management errors, accidents, and data security breaches.
IT departments rely on a combination of strategies, technologies, and education to protect against cyberthreats. Cybersecurity risk management involves identifying your risks and vulnerabilities and applying administrative actions and comprehensive solutions to ensure your organization is protected.
However, risk management is not just an IT exercise. Deciding which risks are acceptable and which are not is a collaboration that must involve senior leadership of the organization.
Luckily, we’ve put together a downloadable guide that highlights the state of IT security and best practices across the association industry. Sound helpful? Download the guide here.
2. Policy management
While many believe that responsibility for cybersecurity sits in the hands of the IT department, security should be a concern for each employee in an organization.
Policies are an effective way to educate employees on the importance of and responsibility for protecting confidentiality, integrity and accessibility of IT systems and data. Cybersecurity policies can be used to set the standard of behavior for all employee activities (i.e. acceptable use policies and confidential data policies).
Grand Theft Data, a McAfee report on data exfiltration found that employees cause 43% of data loss, one-half of which was accidental.
Improved cybersecurity and the management of existing policies can help employees and partners better understand how to maintain the security of data and applications, ultimately lowering the chances of a breach.

3. Vulnerability management
Most organizations depend on a combination of commercial and custom-developed hardware and software to support their IT needs. These technology components inevitably include vulnerabilities in their design, setup, and code. In order to mitigate these risks, organizations must understand said risks and address vulnerability management in a well-defined and managed information security program.
Vulnerabilities are weaknesses that a threat actor (i.e. a hacker, nation-state, disgruntled employee, etc.) can exploit to adversely affect data security. These weaknesses typically focus on issues in the IT software, hardware, and/or systems an organization uses. For example, design, implementation, and other vendor oversights may create defects in commercial IT products.
A robust vulnerability management program can directly address these issues.
4. Education
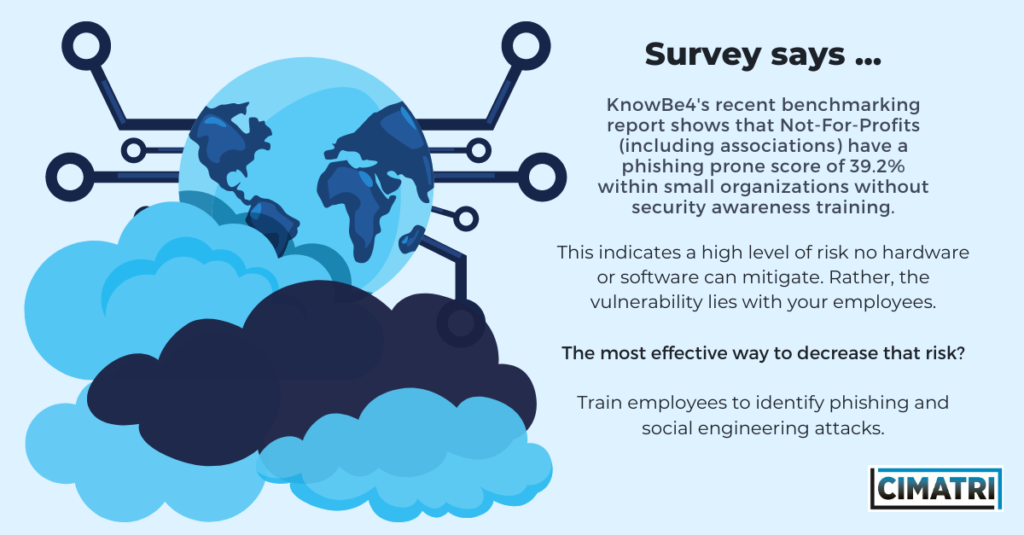
Many organizations still see cybersecurity as an ‘IT thing’. As such, they often forego investments in cybersecurity education. (Read: These organizations have little to no buffer in place to instill a culture of digital resiliency.)
Your employees need cybersecurity training to protect themselves and your organization against cyber attacks. By making employees aware of security risks and threats and what procedures to follow when a threat is identified, you’re strengthening the most vulnerable links in the chain.
New hire training, as well as regularly scheduled refresher training, should be established in order to instill the data security culture of your organization.
Cybersecurity training includes:
1. Company policies and procedures
2. Handling sensitive data used in employee roles
3. Proper ways to store and transmit sensitive data
The Wrap Up
The global cybersecurity threat continues to evolve at a rapid pace, with a rising number of data breaches each year. A report by RiskBased Security revealed that 7.9 billion records were exposed by data breaches in the first nine months of 2019. To put it into perspective, that figure is more than double (112%) the number of records exposed in the same period in 2018.
The average total cost of a single data breach is $3.86 million with the cost of lost business after a breach reaching $4.2 million. And by 2021, more than $1 trillion is predicted to be spent on global cybersecurity.
As such, cybersecurity is more important than ever. It is up to you to ensure that your organization is doing the most to ensure that your organization’s, members’, and employees’ data is protected.
Key Takeaways for Association Leaders
Associations and nonprofits are not immune to these Cybersecurity threats. In fact, a recent study, conducted by CIMATRI security professionals during the 2020 COVID crisis highlights a number of opportunities for improvement in each of these critical areas.
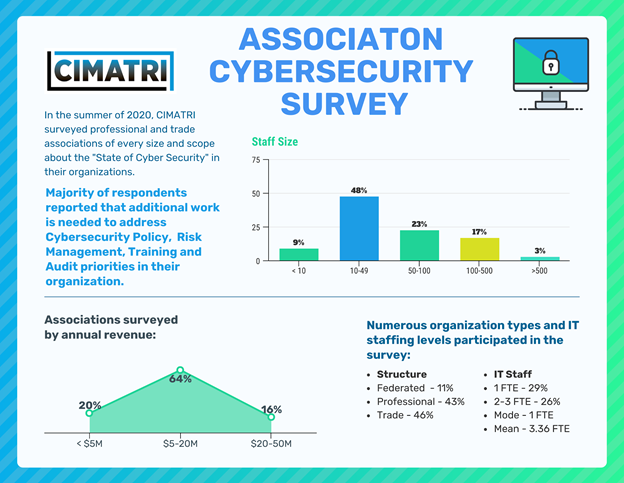
Check out our downloadable guide to see how your strategy compares to others in the association industry.




